Blog
Configure IPS Sensors on FortiGate

By Elias Georgiou – Team Leader of the Implemetation Department
What is IPS?
IPS stands for Intrusion Prevention Systems which are network security/threat mechanisms that perform inline scanning to all network traffic in order to detect and ultimately prevent vulnerability exploits or attacks. Such exploits that come in the form of malicious inputs have as a goal to gain control or interrupt applications or machines.
Intrusion Prevention Systems continuously monitor the network looking to identify possible malicious activities, record information about them, report any detected threats to network administrators and take preventative measures to block a threat from causing any harm. Such preventative measures could be closing access points or configuring firewalls to block any future attacks as well. Intrusion Prevention Systems can also be used to identify issues with company security policies discouraging employees or network guests from violating these policies again.
Nowadays network attackers are becoming more and more sophisticated and can penetrate even the most robust security solutions so IPS have become a key component of all major infrastructures in modern organizations.
How do Intrusion Prevention Systems work?
Intrusion Prevention Systems work by actively scanning all network traffic for known attack patterns or malicious activities which include Denial of Service (DOS) attack, Distributed Denial of Service (DDOS) attack, different types of exploits or viruses. To achieve this, Intrusion Prevention Systems are typically placed behind a Firewall, acting as an additional security layer that performs real-time packet inspection. Upon detecting any malicious or suspicious packets the below actions will take place:
- Termination of the TCP session that was found to be exploited and proceed with blocking source IP address or user from accessing any hosts or network resources.
- Reconfigure the Firewall to block all similar attacks.
- Remove all malicious content within the network by repackaging payloads, removing header information and malicious attachments.
Types of Intrusion Prevention Systems
Most of the Intrusion Prevention Systems use one of the three methods - Signature-based, Statistical-Anomaly based or Stateful Protocol analysis detections.
- Signature-based detection: this approach uses a set of predefined signatures for well-known threats, if an attack is initiated that matches any of these signatures the system will take the necessary action.
- Statistical Anomaly-based detection: in which the Intrusion Prevention System will scan the network for any unexpected behavioural patterns. If any anomaly is found the system will block access to the affected host.
- Stateful Protocol detection: this method requires administrators to create a set of security policies that will apply to the network. If any activity breaks any of these policies an alert is triggered.
Configure IPS Sensors on FortiGate
Fortinet delivers IPS technology via the industry-validated and recognized FortiGate platform. FortiGate security processors provide unparalleled high performance, while FortiGuard Labs informs industry-leading threat intelligence, creating an IPS with proven success in protecting from known and zero-day threats. As a key component of the Fortinet Security Fabric, FortiGate IPS secures the entire end-to-end infrastructure without compromising performance.
To create a new IPS sensor
- Go to Security Profiles > Intrusion Protection.
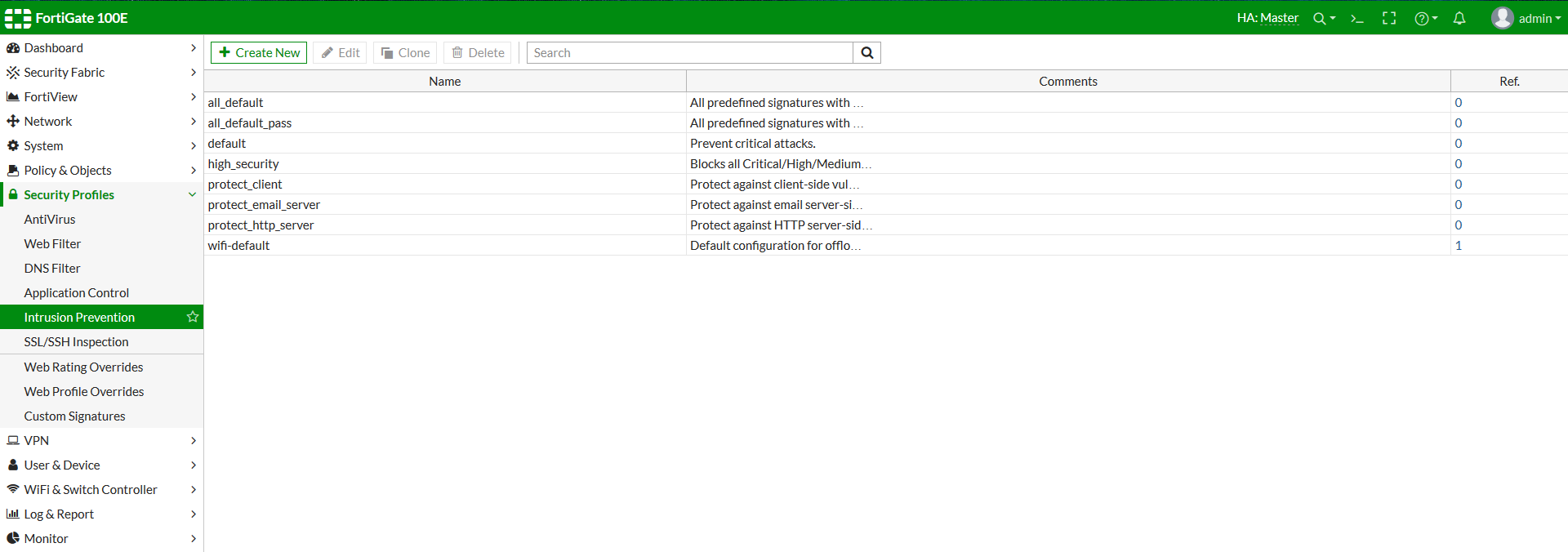
Figure 1: depending on the FortiGate model there are many predefined IPS sensors as well
- Select the Create New icon in the top of the Edit IPS Sensor window.
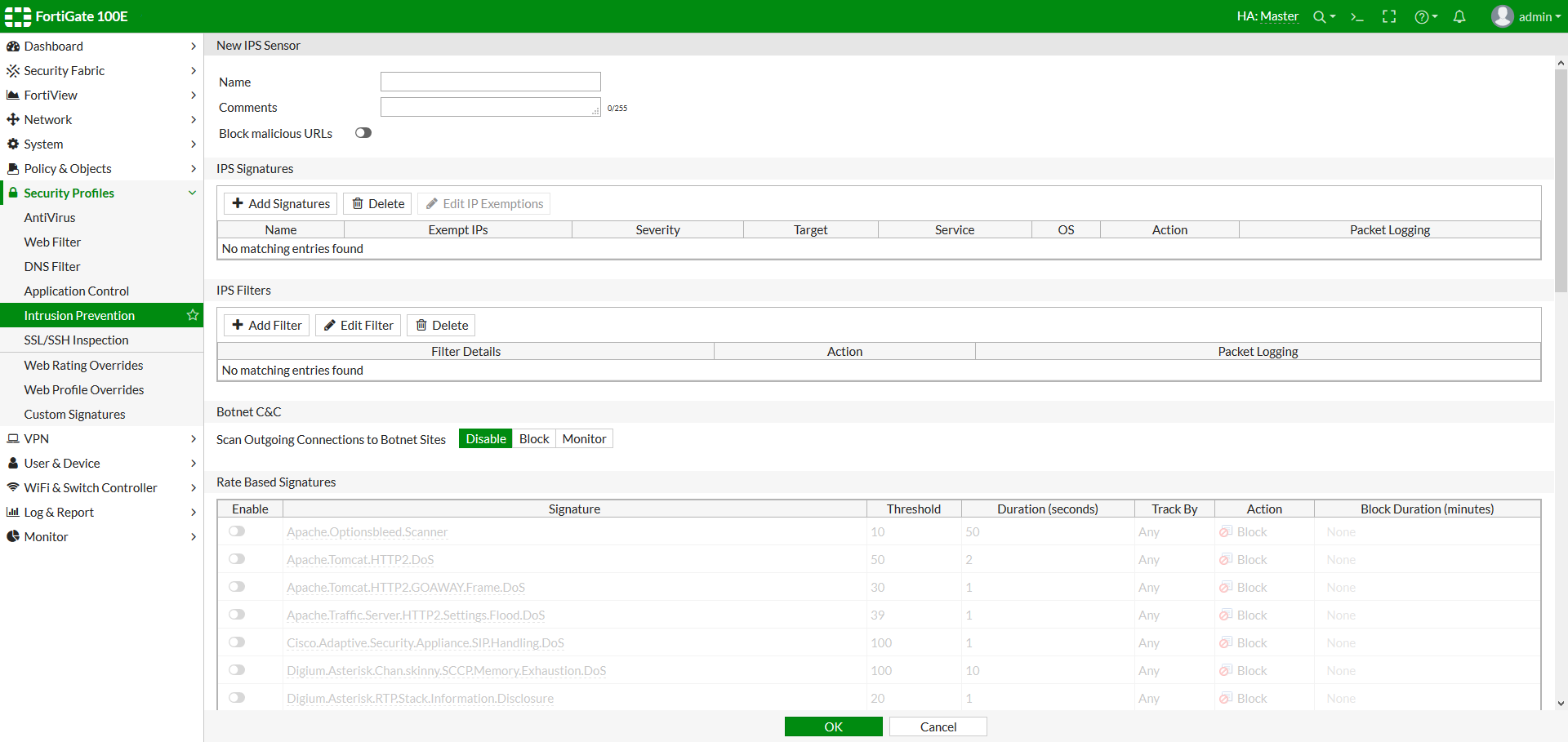
Figure 2: when creating a new sensor, you can add IPS signatures, IPS filters or Role-Based Signatures
- Enter the name of the new IPS sensor.
- Optionally, you may also enter a comment. The comment will appear in the IPS sensor list and serves to remind you of the details of the sensor.
- Select OK.
A newly created sensor is empty and contains no filters or signatures. You need to add one or more filters or signatures before the sensor will be of any use.
To create a new Pattern Based Signature and Filter
- Go to Security Profiles > Intrusion Protection.
- Select the IPS sensor to which you want to add the filter using the drop-down list in the top row of the Edit IPS Sensor window or by going to the list window.
- Under IPS Filters, select Add Filter.
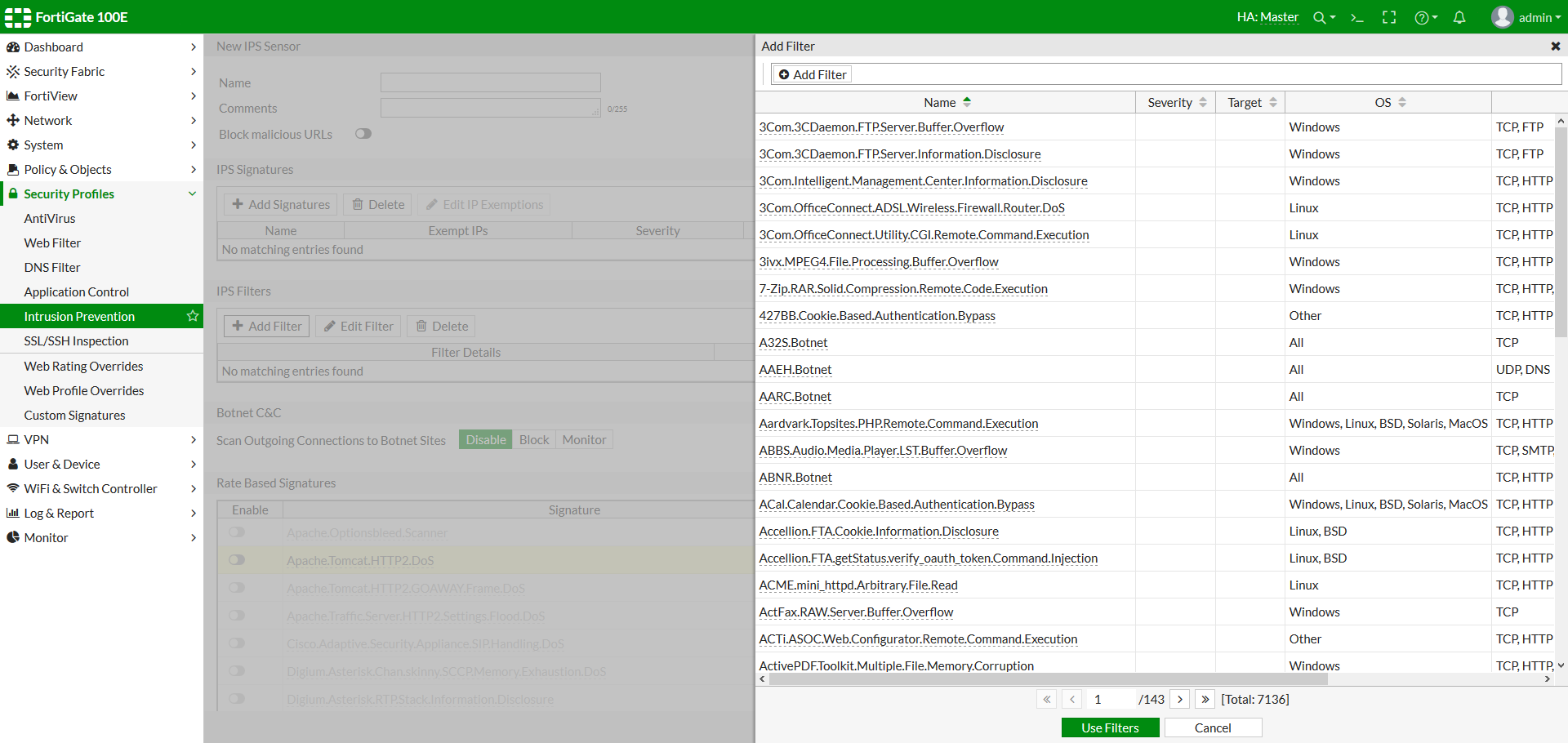
Figure 3: Create a custom filter or select one of the predefined filters
- Configure the filter that you require. Signatures matching all the characteristics you specify in the filter will be included in the filter. Once finished, select Use Filters.
- Application refers to the application affected by the attack and filter options include over 25 applications.
- OS refers to the Operating System affected by the attack. The options include BSD, Linux, MacOS, Other, Solaris, and Windows.
- Protocol refers to the protocol that is the vector for the attack; filter options include over 35 protocols, including "other."
- Severity refers to the level of threat posed by the attack. The options include Critical, High, Medium, Low, and Info.
- Target refers to the type of device targeted by the attack. The options include client and server.
- Once you have selected the filters you wish to add, right-click the filters and choose an action for when a signature is triggered:
- Pass to allow traffic to continue to its destination.
- Monitor to allow traffic to continue to its destination and log the activity.
- Block to drop traffic matching any of the signatures included in the filter.
- Reset to reset the session whenever the signature is triggered.
- Default to use the default action of the signature.
- Quarantine to refuse traffic based on the attacker’s IP Address.
- Packet Logging to enable packet logging for the filter.
- Select Apply.
The filter is created and added to the filter list. The same process can be followed to create or add an IPS Signature to an IPS sensor.
